The Anonymising OJ Repeater
Follow articleHow do you feel about this article? Help us to provide better content for you.
Thank you! Your feedback has been received.
There was a problem submitting your feedback, please try again later.
What do you think of this article?
This is a follow-on article from my earlier ‘What You Can Do In A Day’ post where we set up our Intel Joule as a wireless repeater. Here, as an extracurricular activity, we will take our repeater and modify it so that all our traffic is routed through the Tor network, turning our Joule into an anonymising repeater box. Similar projects on the Raspberry Pi have been called Onion Pi routers, so it seems appropriate to call ours the Onion Joule or OJ repeater.
Getting Tor
It won’t surprise you to learn that we will need to install Tor to get this project going. However, as (according to the Tor Project) the Ubuntu package repository for Tor hasn’t always been updated reliably in days of yore, we will be installing Tor from the Debian repository so there will be a couple of extra steps.
The first thing we need to do is make a couple of additions to our repository list so that the installer will be able to find the Debian repository. From the terminal command line:
$ sudo nano /etc/apt/sources.list
Scroll down to the end where we will add the following:
deb http://deb.torproject.org/torproject.org xenial main
deb-src http://deb.torproject.org/torproject.org xenial main
which should end up looking a bit like this:
Great. Save that and at the command line we will add the gpg key used to sign the packages:
$ gpg --keyserver keys.gnupg.net –recv A3C4F0F979CAA22CDBA8F512EE8CBC9E886DDD89
Followed by:
$ gpg --export A3C4F0F979CAA22CDBA8F512EE8CBC9E886DDD89 | sudo apt-key add -
If it has gone well your terminal will look similar to this:
Now we are ready to install tor with:
$ sudo nano apt update
$ sudo nano apt install tor deb.torproject.org-keyring
When complete, Tor should be installed and running.
Configuring Tor
There are numerous ways to configure Tor for proxy operations, but as we are never really going to be using our Intel Joule as a full-blown network server, we can make life easy on ourselves and simply route all our traffic through Tor as an anonymising middle box. The reasoning is that, as every TCP connection is through Tor, no application from our connecting devices will accidentally reveal our actual IP address by directly connecting to the internet; but we will not be adding routing complexity for filtering local network traffic out of being routed through Tor either. It’s not that efficient for local connections, but as we aren’t making any, it doesn’t really matter.
To get started on this, we need to edit the Tor configuration file (referred to in the Tor documentation as your ‘torrc’) to set Tor as both a transparent proxy and DNS proxy for the devices that connect to our access point:
$ sudo nano /etc/tor/torrc
Near the top of the file, just under the line that says
## Tor will look for this file in various places on your platform## https://www.torproject.org/docs/faq#torrc
You should add the following:
VirtualAddrNetworkIPv4 10.192.0.0/10AutomapHostsOnResolve 1TransPort 9040TransListenAddress 10.15.15.1DNSPort 5353DNSListenAddress 10.15.15.1
It behoves you, of course, to set the TransListenAddress and DNSListenAddress to match the IP address you previously set for your access point. This set-up will listen to our access point address for data traffic and domain name server requests. It also tells Tor that redirected traffic will be forwarded to the internet at port 9040 and DNS requests will be forwarded from port 5353.
What we have to do now is organise the redirection of our traffic. As with our original access point, we will do that with a script.
Scripting Our Traffic Flow
In our script, we will be using Tor rather than kernel IP forwarding as we did with the simple repeater box. This will require some adjustments to our iptables settings. Open a text editor and put in:
#!/bin/bash
MONITOR_DEVICE=wlp1s0OUTPUT_DEVICE=wlx80xxxxxxxxxx # <- set your device namesT_PORT=9040
# Catch ctrl-c for clean exittrap ctrl_c INTfunction ctrl_c(){ echo Killing AP processes... killall dnsmasq killall hostapd}
## If dnsmasq is running, kill it so we can start cleanlykillall dnsmasq
echo Bringing up Access Point interface...ifconfig $MONITOR_DEVICE 10.15.15.1/24 up
dnsmasq
iptables -t nat -A PREROUTING -i $MONITOR_DEVICE -p udp --dport 53 -j REDIRECT --to-ports 5353iptables -t nat -A PREROUTING -i $MONITOR_DEVICE -p udp --dport 5353 -j REDIRECT --to-ports 5353iptables -t nat -A PREROUTING -i $MONITOR_DEVICE -p tcp --syn -j REDIRECT --to-ports $T_PORT
echo Starting Access Point...hostapd /etc/hostapd/hostapd.conf
Remember that you can have hostapd run in the background with the -B option at the end if you prefer. I have left this option off, so I can monitor which mac addresses are logging on to the access point.
Save this file as something appropriate: I called it ‘aptor’. We can then make our script executable:
$ chmod +x aptor
And now we are ready for the moment of truth. Time to fire up our OJ Router.
$ sudo ./aptor
And voila… (Note, it may take a little while to make your original connection to the Tor network) when we connect from one of our devices we see that our IP address is not what it was:
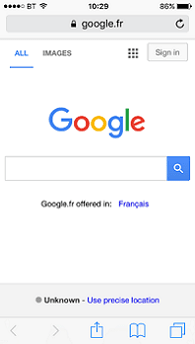
Google.com will also helpfully redirect you to the appropriate local version of Google for your exit node, automatically showing you where in the world your exit node lives:
Unfortunately, Google won’t be very cooperative after that point, as they can’t track you – hence lots of fun ‘Captcha’ screens will follow. Your best bet is to use search sites like Startpage or DuckDuckGo that use Google tech for searching but don’t track your data like Google.
If you have any difficulty getting going, the Tor log is a good place to start your troubleshooting. You can find that in /var/log/tor/log . This is also a great place to see what Tor does while it is logging onto the Tor network.
Final Thoughts
The Tor network is a great part of keeping yourself secure online, but it can only ever be a useful part of your security. Tor does not provide end to end encryption. Any data to and from entry and exit nodes of the Tor network is not encrypted and can be intercepted unless you are using applications that pre-encrypt your data before sending it- for example, at the very least in your browser, use https:// addresses rather than http://.
You can also specify which exit nodes you would like to use by name, fingerprint or country code in your torrc:
ExitNodes {bw},{ug},{vu}StrictNodes 1
This will limit your exit nodes to Botswana, Uganda and Vanuatu. A full list of countries can be found here.
The Tor Project website has a lot of good information about keeping yourself safe online. If you like what they are doing, consider donating.
Stay safe out there!