Providing Secure Remote Access to the PLCnext Can Crusher with mGuard VPN
Follow articleHow do you feel about this article? Help us to provide better content for you.
Thank you! Your feedback has been received.
There was a problem submitting your feedback, please try again later.
What do you think of this article?
Adding remote access for control and monitoring using the Phoenix Contact mGuard VPN.
Introduction
In this article we’ll be taking a look at Phoenix Contact’s mGuard VPN service and running through the full setup procedure to integrate it into the can crusher, allowing remote access for both monitoring and programming purposes.
What is mGuard?
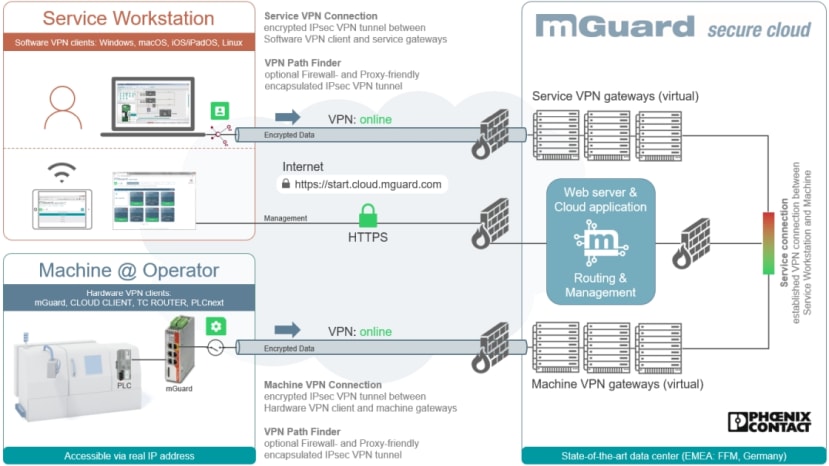
mGuard is the turnkey VPN solution offered by Phoenix Contact, offering a highly secure remote access platform for any machine and production plant within a client network. Utilising the IPsec security protocol with suitable encryption keys helps ensure protection of all data transmitted between service users and machines.
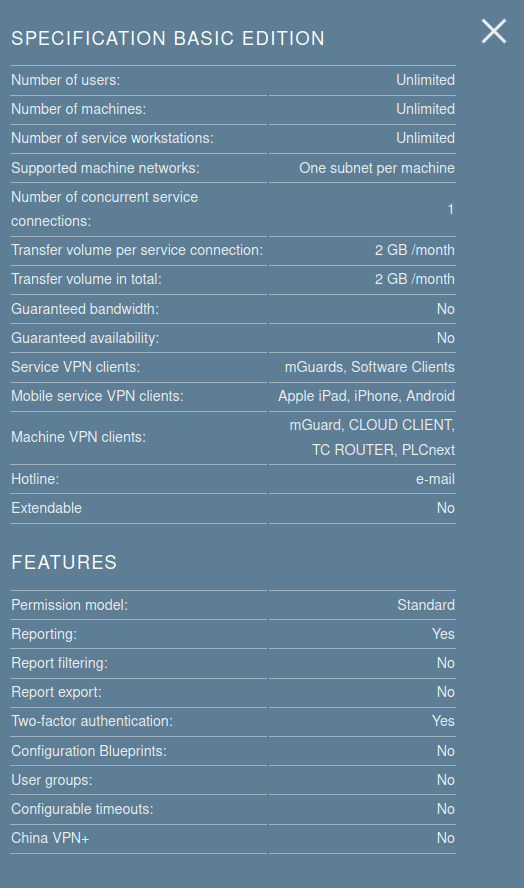
Phoenix Contact offers 24x7 monitoring for the mGuard service, with both email and phone support (depending on the service tier). Two-factor authentication is included by default regardless of the service tier, helping improve security for users. With the premium tier, a bandwidth of 1Mbps is guaranteed, as well as an uptime of 98% annually, amongst a number of other features.
Users and machines located within China can also make use of the mGuard service, with the additional “China+” package. Additionally, the service will also work even with a proxy server in place
As mGuard is hosted by Phoenix Contact, both machines and service users need to be able to connect to the cloud. A variety of ways are offered to do this, including software clients for Windows, macOS, Linux, iOS and Android; as well as hardware clients ranging from a small USB-powered Ethernet connected security appliance (801-7138) , through to DIN rail-mounted routers (255-9489) that offer cellular connectivity and digital IO.
In addition, a web interface is provided that allows access to client information including locations, operators, service targets (machines and plant), VPN users and their access rights.
An at-a-glance view is also presented showing all online machines that can be remotely connected to.
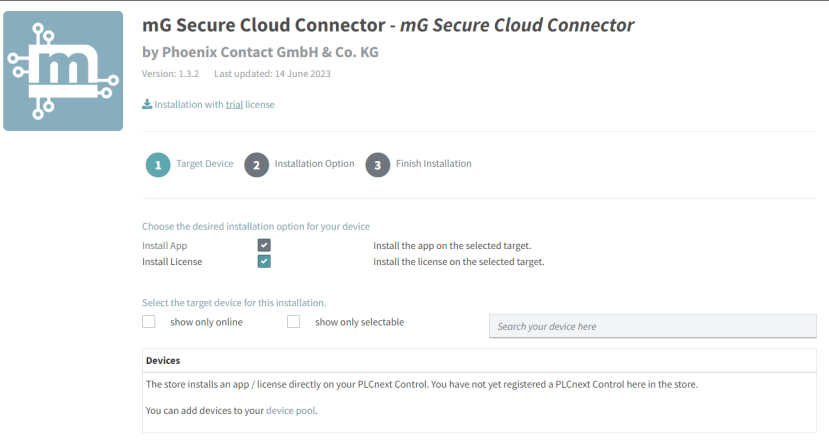
On the machine side, either a hardware router can be used for connectivity to multiple devices, or an application from the PLCnext Store can be run on the PLCnext controllers, at a low cost of €49 for a license, which is ideal for cost or space-sensitive applications.
Setting up mGuard
We opted to set up the mGuard free tier, which includes one concurrent service user connection, with a bandwidth limit of 2GB/month and is more than adequate for our use case.
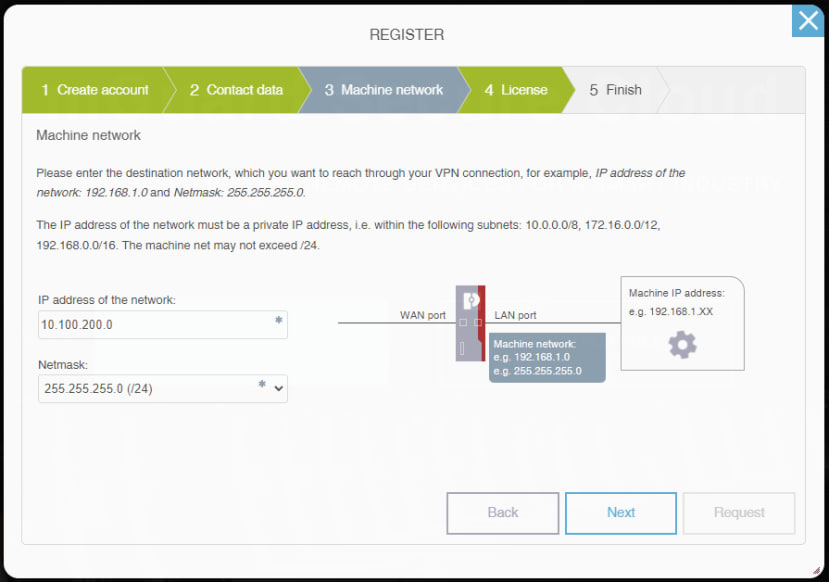
During the account registration process the IP address of the machine network is prompted. We filled this in with the appropriate details, in our case the network is 10.100.200.0/24.
After completing the registration form, an account approval process has to take place. In the meantime, we moved onto installing the PLCnext application.
To install the app directly onto the PLC, a preliminary step of connecting the controller to the PLCnext Store was required. This involves ensuring the controller has access to the Internet, signing into the WBM and then enabling the PLCnext Store services.
A device UUID is then generated which can be entered into PLCnext Store, under “Account” then “Devices”. After some time had passed (around five minutes) once the UUID was added to our account, the controller status changed to “Online”.
The controller then became visible as an installation candidate and successfully set up the application. A reboot was necessary, which we performed from the WBM, at which point the app was installed and running.
With our mGuard account request approved, we started to follow the setup guide to connect both the PLC and a service user.
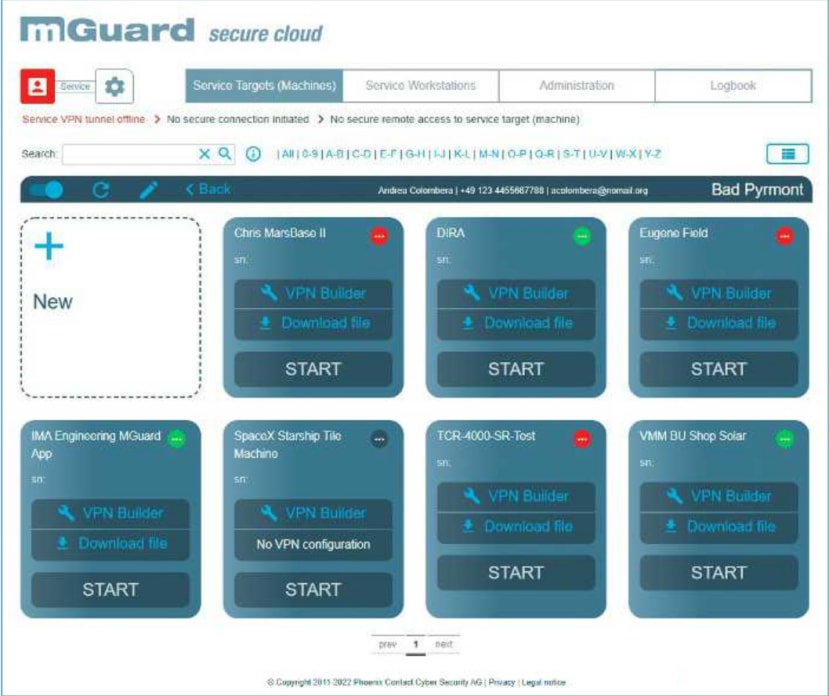
To help keep order within the mGuard overview page, service targets (machines) are required to be grouped under “Operators” (or locations, for example per factory or per client). We created a group and then progressed with adding a new machine.
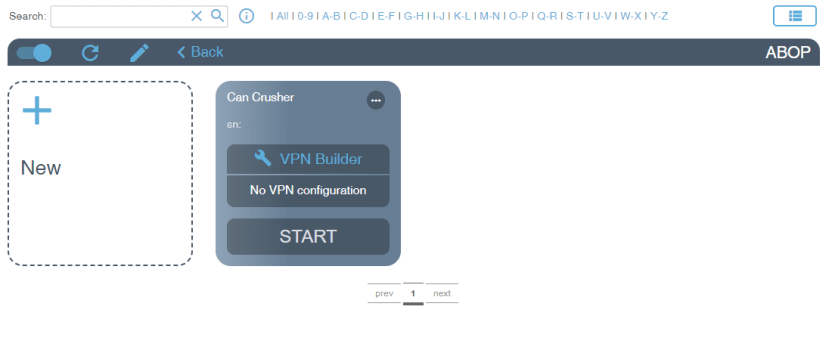
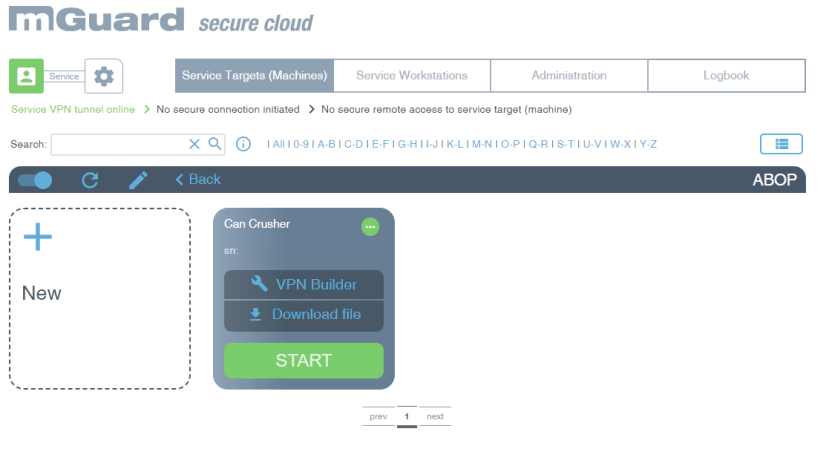
A large “VPN Builder” button appears as no VPN configuration has been produced. The tool walks through setting up a suitable profile ready for uploading into the PLCnext controller. The only information that is required is the PLCnext IP address, plus optional details consisting of a VPN client serial number and email for machine status change notifications.
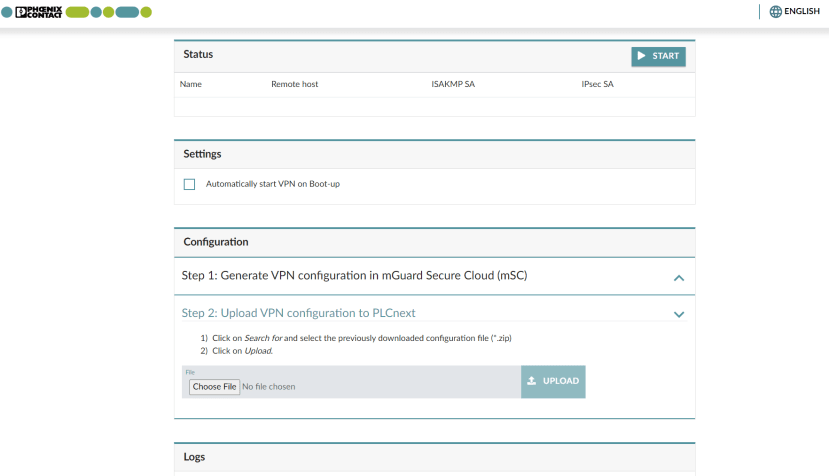
With the configuration file downloaded, it then needed to be uploaded to the PLC. This was done by browsing to the IP address of the controller with “/msc” on the end — in our case “https://10.100.200.1/msc”. A login prompt appeared which accepted the credentials used to connect to the PLC web based management and the configuration file uploaded.
On the secure cloud web interface, a small green dot appeared on the upper right-hand corner of the can crusher machine interface indicating that the VPN was successfully connected.
A service workstation was then created on the mGuard interface. The process was very similar to setting up a machine, including selecting a VPN client type. Two different VPN connection modes are available, including standard IPsec ports 500 and 4500, as well as the “VPN Path Finder” which uses HTTP and can work even behind a network proxy.
We once again downloaded the ZIP archive containing the configuration information ready for testing the VPN connection.
Connecting the VPN
The first step was to install a suitable VPN client that would connect to the mGuard service. A variety of clients are offered, including the official “mGuard Secure VPN Client” from Phoenix Contact (this is licensed, but offers a free thirty day trial), a freeware client from Shrew Soft, as well as clients for macOS, iOS and Android. We opted to try the trial client from Phoenix Contact.
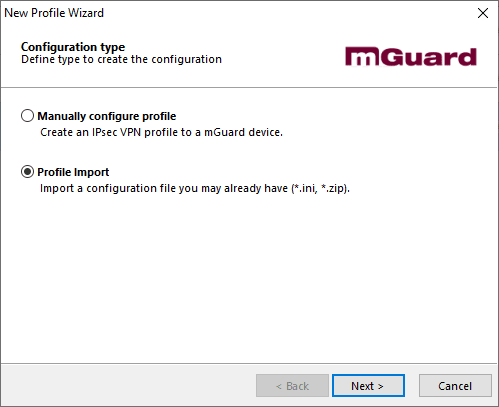
Upon a reboot after installation, the VPN client launched and prompted for a configuration to be either created or imported; as we downloaded the ZIP archive earlier we imported this. Once imported, the big connection toggle was clicked which prompted for the password entered during profile setup, after which a connection to the mGuard secure cloud was established.
Heading back to the secure cloud web interface, the “Service VPN tunnel” status had changed to online, with a green “Start” button appearing on our can crusher device. Once start is pressed, the end-to-end VPN connection is established and we can successfully browse to the web HMI. Remote programming and diagnostics of the PLC can also be performed over the VPN connection, much the same as sitting in front of the device itself, as all traffic is tunnelled.
It is worth noting that the mGuard Secure VPN client routes all traffic from a service workstation over the VPN itself, meaning that the 2GB/month traffic limit could easily be consumed. To alleviate this, a “bypass” function has been provided that can allow other applications to be routed normally.
Conclusion
In this article we’ve taken a look at the Phoenix Contact mGuard secure cloud service that offers an industrial VPN for remote access to machinery and plant equipment.
We’ve explored the hardware and software options available for connecting to the service, as well as setting up the VPN on the PLCnext controller in our can crusher and on a Windows computer. The getting started guide combined with an easy click through setup tool make this process a breeze.



Comments