Texas Instruments TM4C LaunchPad Secure Communication with the Cloud - Part 1
Follow articleHow do you feel about this article? Help us to provide better content for you.
Thank you! Your feedback has been received.
There was a problem submitting your feedback, please try again later.
What do you think of this article?
Part 1: Intro and Software Installation
Secure connections to the IoT. It's an often discussed subject and an often forgotten practice.
We all seem to be a bit lazy when opening our gizmos to the internet. Most examples from suppliers and community don't implement any safety measures. At best, the documentation mentions it a s an exercise left to the reader. More often, it isn't even mentioned.
Most MQTT sample programs (for almost all platforms) teach you to connect over plain http, without a single protection point. That's the shortest path to showing the MQTT functionality. Fast and Easy. But not good enough. Internet connected examples should implement security. Example code proliferates. It's preferable that it's secure code that spreads around the community.
Let's dive into an example that does implement security: the Secure IoT example for the Texas Instruments TM4C Crypto Connected LaunchPad. This project establishes a secure connection to the internet, and sends the internal temperature of your microcontroller as encrypted data.
Hardware needed:
- TM4C129E Crypto Connected LaunchPad
- An internet connected router with a free network port.
Hardware Accellerated Transport Layer Security
We'll use TLS (Transport Layer Security – formerly known as SSL) as the mechanism to protect our communication with the internet. This mechanism encrypts traffic and takes care that only trusted parties (and most likely also spies by now :) ) can decrypt it.
Encryption and decryption requires processing time. Our microcontrollers, with their limited resources, can spend significant time doing that work. Time that we like to use to run our gizmo. In the crypto connected TM4C controller, there is silicon on board that is dedicated to do the encryption and decryption. Executing these processes in hardware gives a significant performance boost to the security processes. That lowers the burden on the microcontroller core. And leaves more free processing time to our gizmo's operation.
Hardware accelerated encryption/decryption
Some of the most expensive encryption and decryption operations are implemented in TM4C129ENCPDT hardware. The list below is a subset of the algorithms (from 43oh)
- Advanced Encryption Standard (AES) hardware-accelerated data encryption and decryption based on 128-, 192-, and 256-bit keysHardware
- Data Encryption Standard (DES) block cipher implementation with 168-bit effective key length
- Accelerated Hash (SHA/MD5) advanced hash engine that supports SHA-1, SHA-2 or MD5 Hash computation
The Secure IoT Sample
The project lets a TM4C Crypto Connected controller talk to the Exocite.
Exocite is a cloud platform that stores your LaunchPad's data and presents it in a browser.
You can show sensor data (and any other information coming from your project) in various ways. You can perform calculations, refresh te data at regular times, …
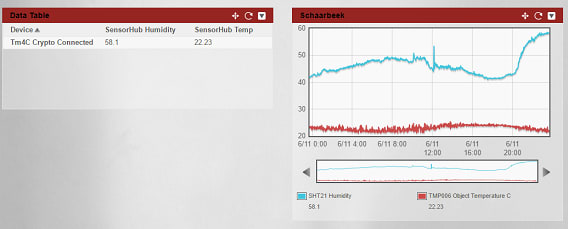
But most of all: you can build a secure connection to Exocite. The program that we build in this blog sends the junction temperature of our ARM core to Exocite (you can extend this example. The image above shows the data of an ambient temperature sensor and a humidity sensor).
Our example builds a secure connection to Exocite – supported by the hardware acceleration modules – and sends the sensor data every 10 seconds.
The blog series is split up in 3 steps:
- the intro and software installation (this blog)
- build TSL libraries and firmware
- register the LaunchPad on Exocite and create a dashboard to show measurements.
Software Installation
The example works with the latest versions of TI-RTOS and the WolfSSL library. But if this is your first encounter with the platform, it is easier to work with the exact same versions that TI used when creating the firmware code. Download the version indicated below and install them. Use the download links. Carefully check that you select the right versions.
- TI-RTOS version tirtos_tivac_2_14_00_10
- WolfSSL 3.6.6
- The firmware source code
This video will help you to complete a successful installation of these packages
BUY A Crypto Connected LaunchPad EvaluationKit
In the next blog posts -
You 'll build the WolfSSL library and the firmware from source code. You'll learn how to check the connectivity with a terminal program. You'll register your LaunchPad on Exocite and start logging data.