Wireless Technology
Follow articleHow do you feel about this article? Help us to provide better content for you.
Thank you! Your feedback has been received.
There was a problem submitting your feedback, please try again later.
What do you think of this article?
It was so much simpler in my grandparent’s day. The ‘wireless’ was a large wooden box in the corner of the room with the soft orange glow of thermionic valves emanating from the back. Its only purpose was to relay the news from Broadcasting House in the refined ‘received pronunciation’ of BBC presenters.
Roll on to the present day: twenty-two years into the 21st century and wireless is a very different beast. Devices capable of bidirectional communication are everywhere and they’re not talking to us, they’re talking to each other. In this article, we briefly review the main wireless technologies for inter-device communication (particularly low-power devices), the kinds of applications for which they are best suited and where their developers are taking them.
Peer-to-Peer Communication
We’ll start our journey with peer-to-peer, which is simply where two devices are wirelessly connected together for direct communication, usually to the exclusion of any other devices.
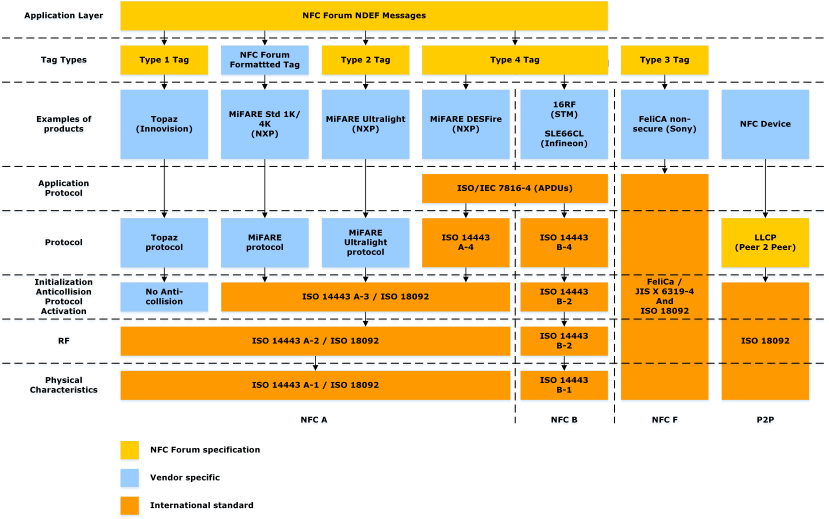
Near Field Communication (NFC)
NFC is a very different animal to all the other wireless technologies we will consider in that it uses electromagnetic fields rather than radio waves for communication. NFC works using magnetic induction, meaning that the reader (an active, powered device) powers its own coil antenna to generate a magnetic field. When another coil is brought close enough, current will be induced in the circuitry of the target (writer) device attached to that second coil.
The two coupled coils essentially form a transformer with an air core, meaning the second device can be completely passive: having no power source of its own. Being powered by the electromagnetic field of the NFC reader device allows the writer to be simple, cheap, small, and to last almost forever, as there are no batteries.
To exchange data, we need a modulation scheme and NFC (ISO/IEC 18092) defines an interface and protocol for a simple wireless connection with a base frequency of 13.56 MHz and a data rate of 424 Kbit/s. The typical range is about 2cm. The NFC communications protocols and data exchange formats are based on earlier radio-frequency identification (RFID) standards, including ISO/IEC 14443 and FeliCa.
The most widespread use of NFC is, of course, contactless payment systems where payment data is encrypted and the extremely short operating range further reduces the possibility of third-party interception of transactions. However, the NFC Forum has defined a variety of modes of operation that allow NFC devices to exchange data in a peer-to-peer mode, emulate a contactless card, be a reader or writer device for tags or cards and transmit up to 1W of power for wireless charging.
The NFC chip market is expected to reach US$ 17.8 billion by 2028, from US$ 8.7 billion in 2021. Two of the largest opportunity areas are currently the integration of NFC with Medical Equipment and the development of NFC-Enabled Wearable Technology.
Bluetooth Classic
Undoubtedly the best-known peer-to-peer technology is what we now call Bluetooth Classic. Although the Bluetooth Special Interest Group (Bluetooth SIG) was formed in 1998, it wasn't until Bluetooth 2.1 + EDR was released in 2007 that the 'Classic' specification solidified and has essentially remained the same ever since. This spec brought Secure Simple Pairing and Enhanced Data Rate mode (with faster modulation, allowing up to 3Mbps throughput) which provided good quality audio for music streaming - just don't engage an audiophile on the subject.
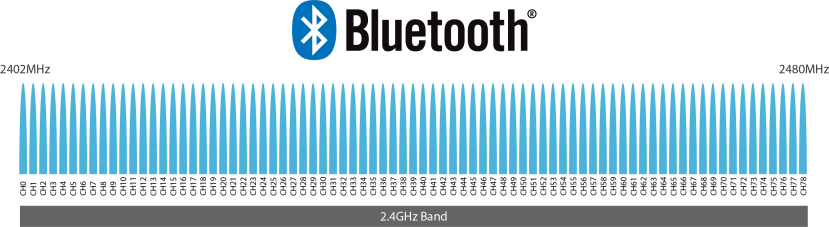
Bluetooth Classic uses the 2.4GHz ISM band which extends from 2400MHz to 2483.5Mhz, though it only uses 80MHz of that bandwidth divided into 79 channels (each with 1MHz spacing) starting from 2402MHz up to 2480MHz. The channels are numbered 0 to 78.
All specifications before Bluetooth 4.0 are now withdrawn and although current Bluetooth 5.2 specs support Classic, the development emphasis is totally on BLE (Bluetooth Low Energy), which we will cover later when we discuss mesh networks.
WiFi Direct
One of the least known, yet most widely available peer-to-peer technologies is WiFi Direct. Android devices have supported Direct since Android 2.3, and Apple devices have had it since iOS 7 (although Apple calls it AirDrop and AirPlay). Most PC chipsets support it as do many entertainment devices (including smart TVs) that make use of it to stream content or screencast from a mobile device.
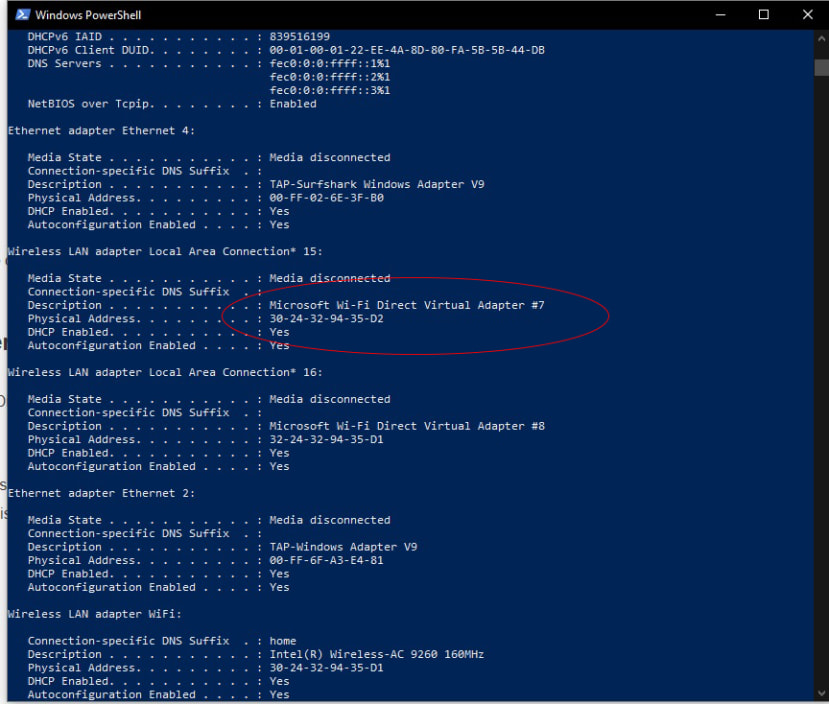
To see if your PC supports it, open Powershell or a command prompt box and type in:
ipconfig /all
If Wi-Fi Direct is available, you should see an entry labelled 'Microsoft Wi-Fi Direct Virtual Adapter'.
Conceptually, WiFi Direct (previously known as WiFi P2P) is a lot like using an Ethernet crossover cable to directly connect the ethernet ports of two computers, without using a switch. Similarly, WiFi Direct allows two computers to directly connect without an intermediary wireless network access point (AP) being involved.
As a side note: there is another IEEE802.11 mode called Independent Basic Service Set(IBSS), also known as Ad Hoc, where two end-points or stations (STAs) are able to communicate directly without the need of an AP. WiFi Direct doesn’t use this mode.
Instead, a Direct device will go through discovery (on Social channels 1, 6 and 11 in the 2.4GHz band) to find another Direct device and form a P2P Group. Devices negotiate who is going to take the AP role, known as Group Owner (GO), during the group formation procedure. Once this procedure is completed, the Direct Group will act as a wireless network on IEEE 802.11 infrastructure mode, enabling legacy devices (IEEE 802.11 a/b/g/n/) to discover and connect to the P2P Group. Operation can be in either 2.4GHz or 5GHz bands. The SSIDs for Direct have to start with the Wildcard SSID(DIRECT-), so they are easily recognized. Devices that are not in the role of a GO are not discoverable by an STA performing either a passive or active IEEE 802.11 scan.
Why use WiFi Direct over Bluetooth? In a word: speed. A Wi-Fi Direct-certified device supports typical Wi-Fi speeds, which can be as high as 250 Mbps but this comes at the cost of higher power consumption. This makes Direct a great solution for fast sharing of large files, syncing device information, screencasting / screen-sharing and gaming where power usage is not the major concern. However, due to that heavy power use, WiFi, in general, is not a great solution for low-power devices so we will leave it out of our further discussions – but if you’re curious about the technology, you can check out my previous article on the latest iteration of WiFi 6.
Mesh Networks
Moving on, the next technology to consider are mesh networks. The essential feature of mesh networks is that devices do not require a direct link in order to communicate. Instead, devices can communicate via almost any number of intermediary devices who will recognise the message is not for them and pass it on down the chain to the final recipient. As each device is only transmitting over a short range, the radio gear for each device can have a pretty low power consumption: allowing the creation of a huge network of devices, covering a very large area, that are battery operated with the expectation of a sensible battery life.
There are four common technologies used for building this type of low-power, low-data network: Bluetooth Low-Energy, Zigbee, Z-Wave, and 6LoWPAN.
Bluetooth Low Energy (BLE)
Bluetooth Classic, as it is now called, was originally conceived as a replacement for wired serial protocols like RS-232C but went on to support almost three dozen different profiles including hands-free devices, human interface devices and much more.
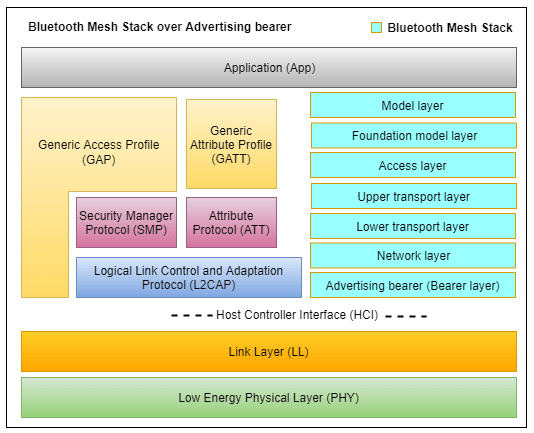
In 2010, as part of the Bluetooth 4.0 spec, Bluetooth Low-Energy (BLE) was introduced. It was known as 'Bluetooth Smart' clearly indicating that it was targeted at Internet of Things (IoT) applications with devices like broadcast-type sensors (e.g., temperature, humidity, etc.) that do not require pairing.
The Mesh Profile was released in mid-2017 to roughly correspond with the availability of new Bluetooth 5 devices that brought additional speed and distance options. Interestingly, the mesh profile will work with any Bluetooth 4.2 compatible devices, as well as Bluetooth 5 devices. This means that most smartphones, tablets, and laptops (which have built-in BLE chips) only need a software update to support Bluetooth mesh - a major advantage for Bluetooth mesh over its competitors.
The maximum number of nodes supported by Bluetooth mesh is 32,767, with up to 4,096 subnets and 65,535 scenes. Subnets allow for segregating the network into logical functions: for example, different floors of a building in a building control scenario. Scenes are a collection of settings such as lighting or HVAC pre-sets for different environmental conditions.
Unlike IP-based networks, Bluetooth Mesh uses managed flood routing for forwarding messages from one node to another. In this model, messages are not routed along a specific path but broadcast to each node in the vicinity for relaying. All packets include a time-to-live (TTL) field, limiting the number of hops to 127 (each hop decrements the counter) and a network can determine its own topology (using Heartbeat messages) and set TTL to the exact number of hops needed. Each device also contains a message cache and can determine if it has seen a message before and if it has, immediately discard the message, removing the potential for routing loops.
Devices which are very power-constrained, such as sensors powered by small batteries which must last for years, may be designated “low power nodes” and exempted from relaying messages.
The advantage of this method is robustness: there is no need for any devices to act as routers, the failure of which could render a section of the network inoperable. However, it may be difficult to build determinate network applications as latency and performance will depend on the network scale and conditions.
With an extensive feature set, including support for beacons, BLE mesh is a strong candidate for a wide range of applications including building management, asset tracking, localised navigation (within a convention centre, for example) and even its most widely known use: as an audio transmission medium with the recently announced Auracast™.
The Bluetooth SIG has a long list of specifications in development, so the future of this technology looks bright.
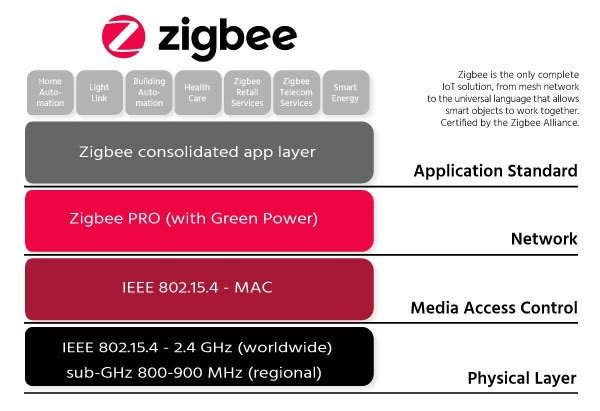
Zigbee
Where Bluetooth started life as IEEE 802.15.1, Zigbee is based on another wireless personal area network (WPAN) radio standard, IEEE 802.15.4 which defines the physical (PHY) and Media Access Control (MAC) layers. The Zigbee protocol is built on top of these layers and was designed out of the gate for creating low-power, low data rate, and close proximity (up to 75-100 meters) wireless ad hoc networks.
Zigbee operates in the unlicensed ISM bands:
Channel 0: 868 MHz (Europe)
Channel 1-10: 915 MHz (Americas and Australia)
Channel 11-26: 2.4 GHz (worldwide)
Note: some devices also use 784 MHz in China.
Data rates and modulation methods vary across the bands. In the 2.4 GHz band, there are 16 channels with 5MHz spacing. Modulation is offset quadrature phase-shift keying (OQPSK) providing a raw data rate of 250 kbit/s per channel. Binary phase-shift keying (BPSK) provides raw data rates of 40 kbit/s per channel in the 915 MHz band and 20 kbit/s in the 868 MHz band.
The Zigbee network architecture is built on three classes of devices:
Zigbee Coordinator (ZC): Every Zigbee network has at least one coordinator which acts as the root of the network and may bridge to other networks. It acts as the trust centre to initiate the network and store information, like routing tables and security keys.
Zigbee Router (ZR): acts as an intermediary device, allowing data to pass through to other devices, often while running application functionality too.
Zigbee End Device (ZED): has limited network functionality, enough to communicate with a parent node (either the coordinator or a router) and then (usually) be in a sleep mode most of the time to enhance battery life.
Together, these device types facilitate building network architectures such as star, tree, or mesh depending on the application. A mesh network can theoretically include up to 65,000 devices and, like BLE, uses 128-bit AES encryption.
Introduced by the Zigbee Alliance in 2005, the protocol was updated in 2006. Zigbee Pro was introduced in 2007. Disparities in routing options mean that Pro devices must act as non-routing ZEDs on legacy Zigbee networks - and vice versa on Pro networks.
Zigbee is supported by a large number of blue-chip manufacturers in the Zigbee Alliance (now the Connectivity Standards Alliance) so it remains a great, low-cost solution for a range of automation applications including Smart home; Security monitoring and control; Smoke, water and gas leak monitoring; Healthcare devices; energy management applications and Food safety monitoring.
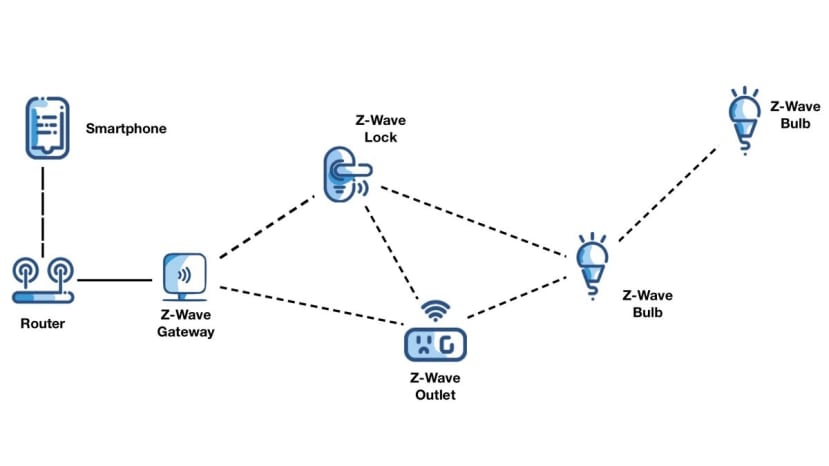
Z-Wave
The Z-Wave protocol was originally developed as a proprietary system on a chip (SoC) home automation protocol by Danish company Zensys in 1999. When it started gaining traction with automation manufacturers, the Z-Wave Alliance was formed in 2005. Roll on to August 2020 and the Z-Wave Alliance re-incorporated as an independent non-profit standards development organization with seven founding members from a consortium of over 300 companies. As of 2022, there are over 4,000 separate Z-Wave certified interoperable products on the market.
The intent behind Z-wave is toward home automation rather than industrial applications and there is a 232-node limit on a standard Z-Wave mesh network.
Technically, it is a low-latency, small data packet protocol supporting data rates up to 100kbit/s and also uses the Part 15 unlicensed ISM bands with the exact frequency dependent on your location.
The standard modulation scheme is frequency-shift keying (FSK) with Manchester encoding but GFSK and DSSS-OQPSK are also supported. The range is up to 50 meters indoors, rising to as much as 200 meters line of sight outdoors. Z-Wave uses the same AES-128 symmetric encryption as Zigbee.
A Z-wave network is centred around a controller (often referred to as a smart home hub), which acts as a gateway device to the home TCP/IP network. Each Z-Wave network has a unique 32-bit ID, preventing devices on different networks from talking to each other. The network is formed automatically as router-capable devices are added, forming a loose mesh. The ‘inclusion’ process allocates each device a unique 8-bit node ID and adds encryption keys plus a map of the signal strength to nearby devices for message routing.
Z-wave is another technology that has strong backing from a lot of big players. It is also selling well, even if users are not necessarily aware of the technology – Ring alarm systems, for example. This makes it a strong contender for many ‘smart home’ applications.
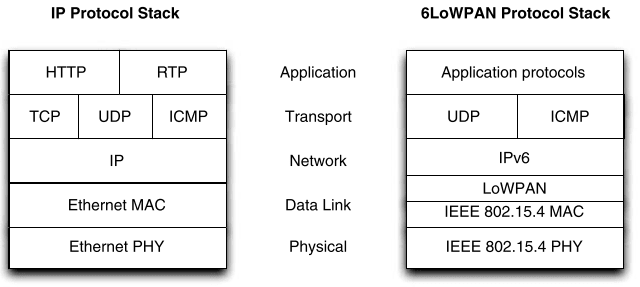
6LoWPAN
The prize for the oddest name definitely goes to 6LoWPAN. It's an acronym for IPv6 over Low-Power Wireless Personal Area Networks.
However, although it uses IPv6 at the network layer, 6LoWPAN is another technology that uses IEEE 802.15.4 for the PHY and MAC lower layers. An intermediate adaptation layer handles the interoperability issues that arise from IPv6 having a minimal possible MTU (maximum transmission unit) size of 1280 bytes, which is considerably longer than IEEE802.15.4's (power consumption conscious) standard packet size of 127 octets. The setup allows for large-scale connectivity while supporting low-power devices.
6LoWPAN also uses 128-bit AES symmetric-key encryption (that provides 3.4x1038 possible key combinations) for security.
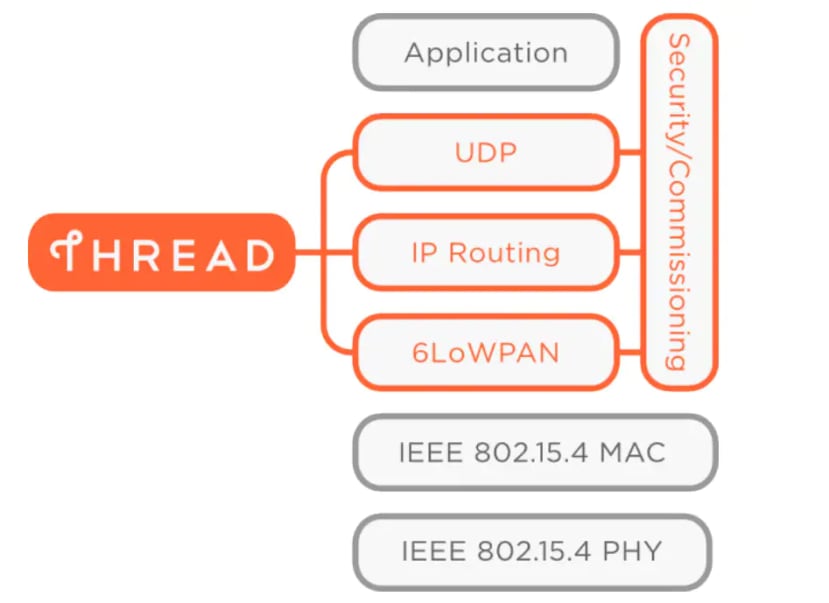
The thinking behind 6LoWPAN (and mesh networking protocols like Thread, built on the standard) is that as the internet runs on IP, the Internet of Things should too. They should seamlessly integrate with larger IP networks without proprietary gateways or translators. Using IPv6 extends the number of possible IP addresses to a lofty 2128, so they shouldn't run out any time soon.
In terms of backing, Thread was developed by Nest and is integrated into the Nest Thermostat, though it's currently not used. Google bought Nest for $3.2 billion and is a major champion of the protocol, along with other members of the Thread Group, which is another who's who of tech industry heavyweights.
With open-source code and big backing, this is another technology with a good chance to dominate the building control/smart home industry.
Long Distance Low Power Technologies
For devices that need to be in remote locations and must operate on battery power for a year or more between maintenance visits, then a low-power, long-distance radio scheme is essential.
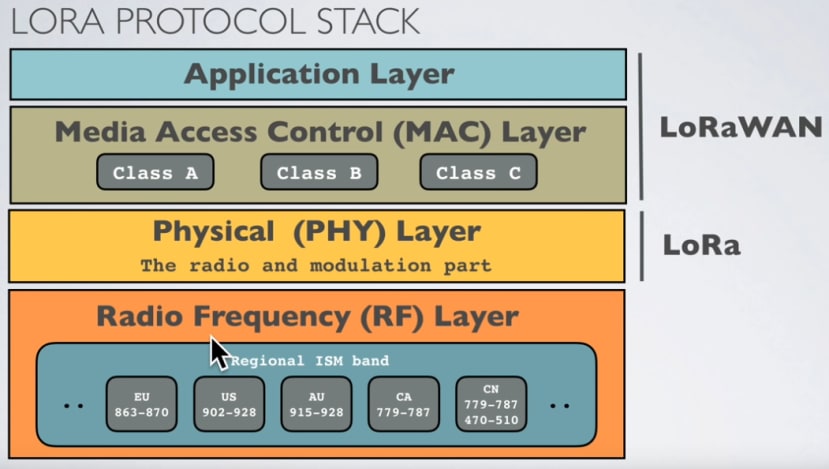
LoRaWAN
If you have been in the IoT space for any length of time, LoRa (as in Low Power, Long Range) is probably the first thing to come to mind when thinking about communicating over large distances. It is another technology to come out of the IEEE 802.15.4 standard and uses the same ISM bands, though it can also operate on the 2.4GHz band for higher data rates at the cost of the range.
LoRa is a proprietary radio communication scheme originally developed by French company Cycleo, which has since been acquired by Semtech. The modulation scheme is a derivation of chirp spread spectrum (CSS) which uses wideband linear frequency modulated pulses (that increase/decrease in frequency over time) to encode data. It is robust against channel noise and multi-path fading, making it great for long-distance messaging at low power. Data rates are between 0.3 kbps to 5.5 kbps with a line of sight range of up to 15km and a maximum payload length of 243 bytes.
While LoRa describes the physical layer, it is the layers above (MAC and application) that make up LoRaWAN, as a routing protocol to manage communication between LPWAN gateways and end-node devices.
LoRaWAN gateways are usually mains-powered devices that relay LoRaWAN packets between end devices and network server without knowing any device-specific information and do not handle any cryptographic keys.
LoRaWAN supports 3 classes of device in the spec:
Class A - (All) An end node can broadcast a signal at any time. Each device uplink to the gateway and is followed by two short downlink receive windows.
Class B - (Beacon) In addition to Class A receive slots, class B devices open extra receive slots at scheduled times synchronised to a beacon from the gateway.
Class C - (Continuous) Same as A but these devices are continuously listening and so are often mains powered.
There are strict Time on Air (ToA) and Duty Cycle (proportion of time a device is operated) limits for data broadcasts – for example, in Europe there is a 0.1% and 1.0% duty cycle per day limit depending on the channel.
As LoRaWAN networks can also determine the location of devices using triangulation (without needing GPS technology) LoRaWAN is a good fit for a range of remote tracking and management functions in areas like: air quality/pollution monitoring, facilities/infrastructure management, health monitoring and management, livestock management, flood and irrigation control, Fire detection and management, hazard (e.g radiation) and leak detection to wherever your imagination takes you.
Although LoRaWAN has restrictions in terms of a downlink transmission, transmission intervals, latency, and bandwidth to achieve long-range and low-power, the LoRa Alliance (with more than 500 members) has shown genuine innovation in solving real problems in a number of sectors.
Public Network Technologies
The other long-range alternative is to connect to a pre-existing network operator Like Sigfox or a cellular network.
Sigfox is a network operator founded in 2010, that has had a rough year in 2022, slipping into receivership before UnaBiz took over in April. It is built as a global, dedicated to IoT network, using its own base stations deployed across various countries around the world, though coverage is far from complete in most regions. Sigfox uses unlicensed ISM bands and end devices connect to base stations using BPSK (Binary Phase-shift keying) modulation with a bandwidth of 100 Hz and a maximum data rate of 100 bps. Intended for sensors, it has limited half-duplex communication with a maximum number of uplink messages of 140 per day with a payload of 12 bytes and only 4 download (8 byte) messages per day. There are 333 different channels and a range of 10 km in urban and 40 km in rural areas.
NB-IoT (or Narrowband Internet of Things) is Cellular LPWAN which uses low-cost modules connecting to existing cellular infrastructure for data transmission. It has a bandwidth of 180 kHz, which equates to one resource block in GSM and LTE. Transmission is FDMA (Frequency Division Multiple Access) in the uplink and OFDMA (Orthogonal FDMA) in the downlink with a 66 kbit/s data rate and it can connect in the order of 100 000 devices per cell and even that number can be increased by using multiple NB-IoT carriers. Payload length is a maximum of 1600 bytes and an unlimited number of messages can be sent per day.
LTE-M is another Low Power Wide Area (LPWA) technology and stands for Long Term Evolution for Machines. Like NB-IoT, it is a 3GPP Release 13 (LTE Advanced Pro) specification. Where NB-IoT is aimed at low data rate, fixed devices LTE-M supports a much higher 1.4MHz bandwidth for peak uplink/downlink data rates of 1Mbit/s with only 10 to 15ms latency (compared to 1.6 to 10 seconds for NB-IoT) making it more suitable for mission-critical real-time applications. It can also handle voice over the network and cellular handovers allowing assets to be mobile and roam across the network. There are no use cases for NB-IoT that LTE-M is unable to cover, but you will be paying for that extra bandwidth.
Both NB-IoT and LTE-M are low-power and should support long battery life, depending on the use case. Both are really still in roll out, so coverage may be a determining factor in which tech can currently be used for an application.
Final Thoughts
As there is so much choice in device-to-device communications I have, of necessity, had to be brief. If I have missed your favourite wireless tech, I apologise – but please feel free to mention it (and its merits!) in the comments.
With so much investment from big players, who are often investing in ostensibly competing tech, it is clear that the industry as a whole has placed a big bet on these technologies to carry them forward. As long as the IoT market grows, even at the low-end of expectations, it will be a tide that is great enough to allow most of these technologies to find a profitable niche for the foreseeable future. So, I expect that only one or two of them will have fallen by the wayside by the end of the decade.
But what do you think? Is there a real ‘Betamax’ among the technologies I have mentioned?